Welcome to the eighth – and final – week of recordings from the Dyalog User Meeting in Belfast! I’d like to take this opportunity to thank all the speakers who helped make Dyalog ’18 another valuable experience! Fittingly, we’re wrapping up with a larger, and even more varied collection than usual: two talks by members of the Dyalog team, two by users of Dyalog APL, and one from the British APL Association – five in total!

1. There are big changes afoot at the British APL Association and Paul Grosvenor, the chairman of the BAA, took to the stage in Belfast to tell us about them. Most importantly, the Vector magazine is going online after 25 years as a printed publication – and the removal of printing costs means that membership is now free! An annual conference in April/May is being planned. There has never been a better time to join the BAA, and you don’t need to live in the UK to do so! In addition to watching Paul’s talk, you can read about many of the changes here and on the new vector website (coming soon!).

2. Arianna Francia from SimCorp Italiana works in one of the largest APL development teams in the world. IFRS 9 is an International Financial Reporting Standard (IFRS) promulgated by the International Accounting Standards Board (IASB). Fortunately, although Arianna’s talk is titled “The IFRS 9 Project”, she completely avoids the subject of IFRS, and instead offers valuable insights into how a rapidly growing team, faced with an extraordinarily complex project, adapted and adopted a combination of agile practices and ideas from Ed Catmull’s book Creativity, Inc, which is about his experience managing Pixar.
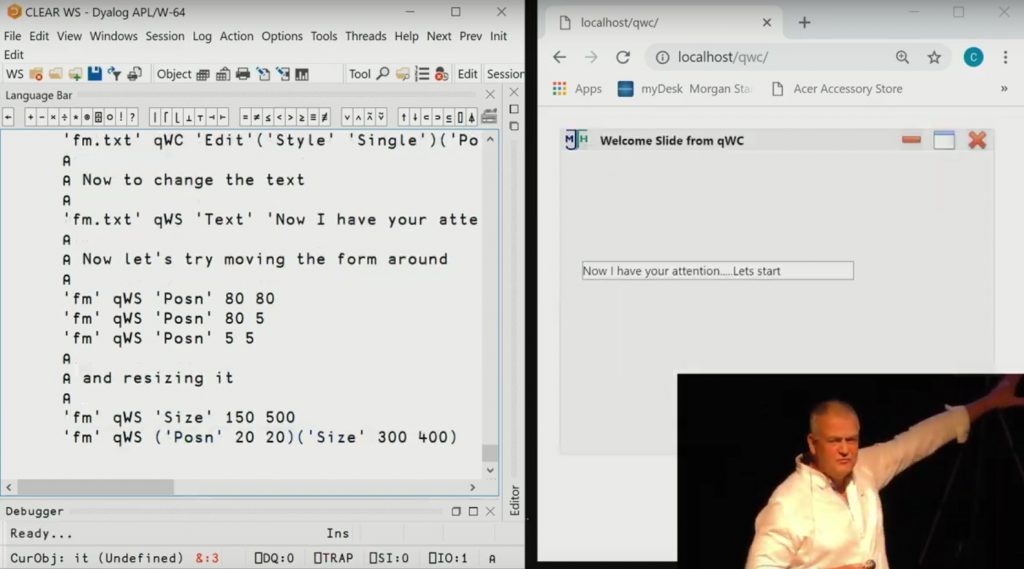
3. For many Dyalog users, the least attractive aspect of Dyalog’s MiServer as a tool for cross-platform user interfaces is that it comes with a completely new set of controls or “widgets”, which essentially means you will need to rewrite your ⎕WC-based user interface. If you are facing this problem, Chris and Michael Hughes have very good news for you: in their talk “⎕WC on the Web”, they demonstrate a new tool that emulates ⎕WC, allowing you to create your UI in a web browser or the HTMLRenderer component included with recent versions of Dyalog APL.
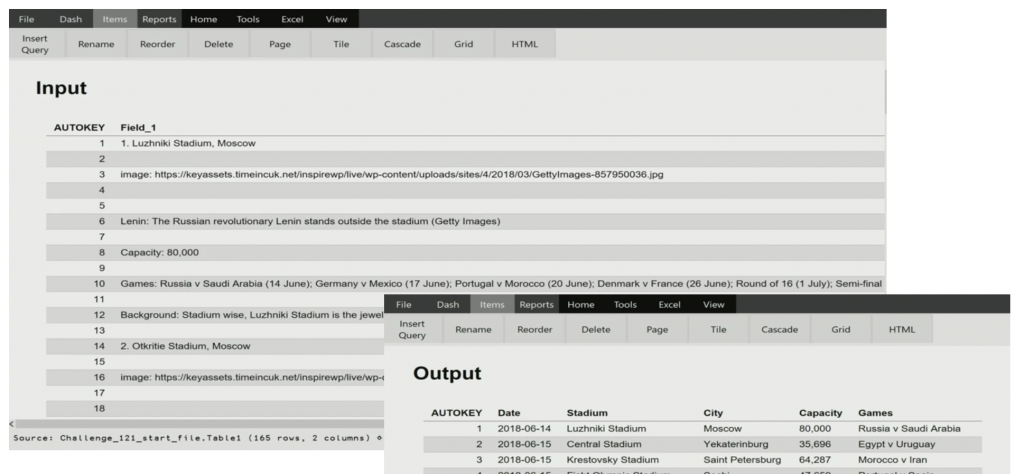
4. Nested arrays make it easy – sometimes, too easy – to represent tables as 2-dimensional arrays. However, if each column of a matrix has the same data type, there are very significant savings to be had in both space and time if you “invert” such tables and represent them as a list of vectors, each containing the values for one column. In his talk on “Inverted Tables”, Roger Hui evolves a set of short, elegant and efficient functions for common operations on inverted tables.
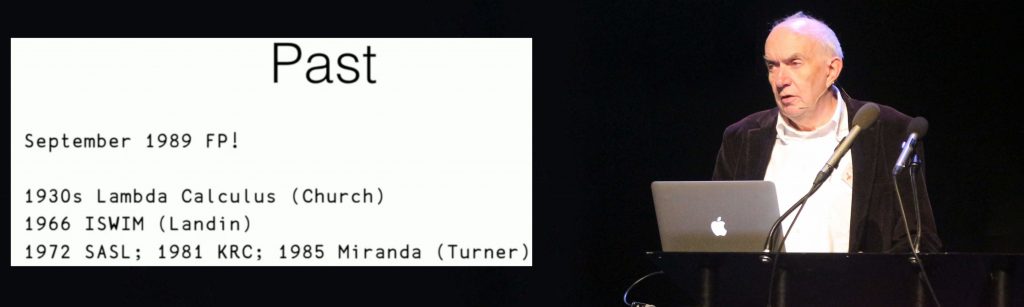
5. It appears that the APL community came very close to losing John Scholes after he read the September 1989 edition of British Computer Journal special edition on Lazy Functional Languages and was struck by the beauty of functional programming. Fortunately, John decided to work on functional extensions to APL, and came up with dfns. This new notation was added to APL in 1996, only six years after Haskell 1.0 appeared. In his talk entitled “dfns, past present and future”, John revisits the early days and muses about things that could have been done differently, but quickly moves on to talk about ideas for future extensions to dfns, like guarded guards, where clauses, and optional type specifications.
I hope that you enjoy watching your choice of recordings as I have enjoyed revisiting them in order to write about them. As you may have noticed, we have taken a break from webinars while we have been rolling the Dyalog’18 recordings out. Now that we’re done, remember to set time aside at 16:00 (U.K. time) on the 3rd Thursday of each Month to follow the webinar series. The next webinar will be on Thursday February 21st: a presentation by our CTO Jay Foad, on his adventures as a participant in the Advent of Code programming competition, which was held in December.
Summary of this week’s videos:


 Follow
Follow






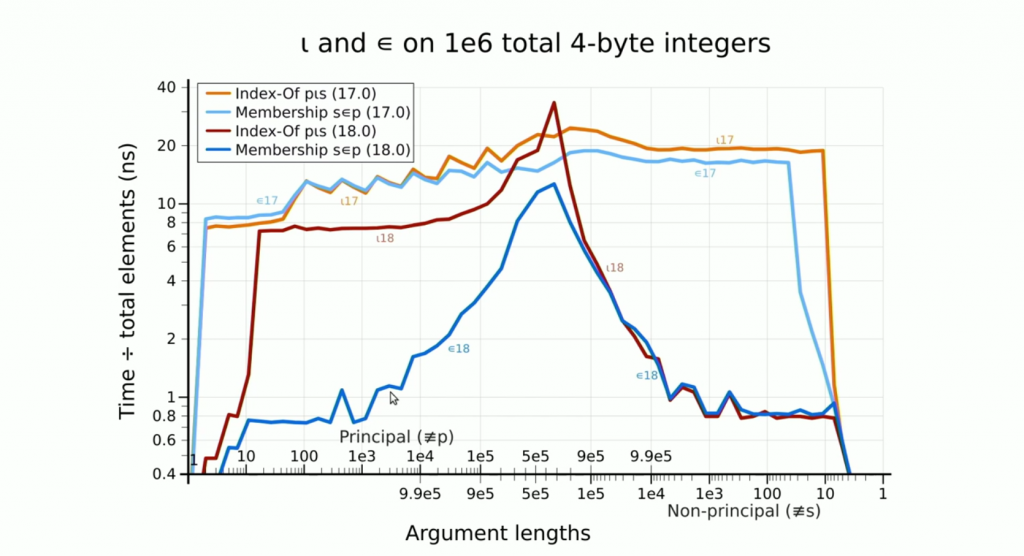
 By combining non-branching algorithms with vector instructions and a technique known as Robin Hood Hashing, Marshall is able to drive a modern CPU close to the theoretical maximum throughput, and in many cases spend less than one nanosecond searching for each item of an array.
By combining non-branching algorithms with vector instructions and a technique known as Robin Hood Hashing, Marshall is able to drive a modern CPU close to the theoretical maximum throughput, and in many cases spend less than one nanosecond searching for each item of an array.